Increasingly sophisticated MFPs and the importance of security management
By Shinichiro Oda, Regional Manager Infosource Japan
Looking at Multi-Function Printers (MFPs) from the perspective of preventing information leaks, from a functional and operational standpoint, we know that there are significant risks associated with the operation of these devices. If the MFP is accessible from the Internet, it could become a potential target for hackers. This risk exists even if the MFP is located within a LAN protected by a firewall. Without implementing the appropriate network security measures, there is a possibility that copied or scanned information can be surreptitiously extracted.
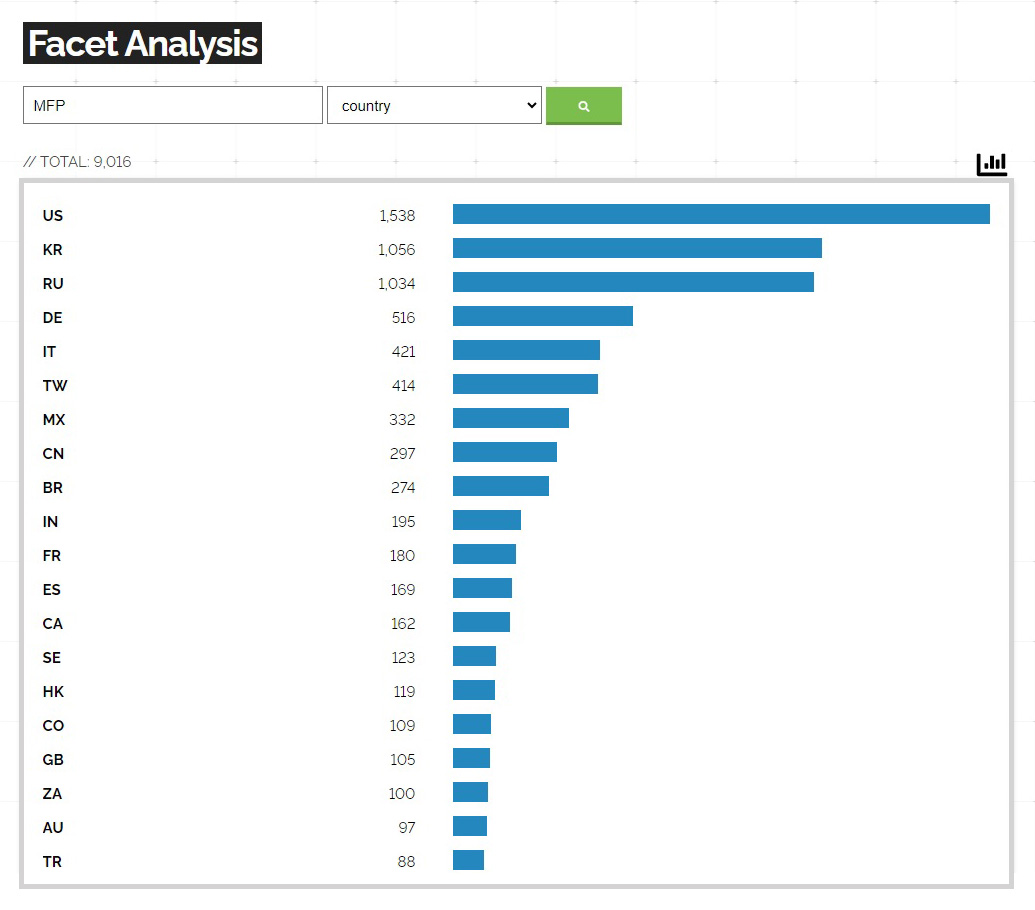
As to emphasis this point Fig. 1 shows the results of a search for the keyword MFP on SHODAN, a hacker-friendly website that allows users to search for devices on the Internet and shows how many MFPs are exposed to the public Internet. One can imagine that if the administrator password is left as the default, it could be easy to view or download the scanned or copied images from the history information.
In addition, MFPs usually have a built-in Apache-based Web server that allows the user to remotely control the MFP, so that if the user ID and password are known, the data in the MFP can be viewed from anywhere in the world.
Fig. 2 by country, it shows that the U.S. has the overwhelming number of addresses directly connected to the Internet, followed by South Korea and Russia.
This situation is unlikely to be the result of an intentional act by the network administrator of an organisation, and more likely to be the result of universities and research institutes that have been allocated an abundance of global addresses.
Although MFP vendors incorporate a variety of measures and features to prevent information leaks. Information leaks cannot be prevented unless the MFP is installed, configured, and managed by the organisation’s network administrator utilising appropriate built-in design features.
The security features implemented by most MFPs today include:
- Restriction of operable functions by administrator password
- Restrict operable functions and protect documents by user authentication
- Setting access rights/restricting and controlling web server functions
- Restricting/controlling server functions
- Restrictions through IP filtering
- Firmware updates
- Other security features (e.g., preventing fax misdirection, setting passwords for scanned documents, encrypting hard disks and other storage devices)
These implement the same or better functionality of general network servers and are considered as security measures from both a technical and human aspects, such as hacking, spoofing, eavesdropping, mishandling, and forgetting, proper configuration and thorough organisational operation rules are essential.
Will scanners require the same security measures that MFPs have evolved?
MFPs have evolved into essential office equipment devices that offer a range of document solutions. These solutions encompass duplicating various documents generated in office work, sending/receiving faxes, and providing printing and network printer capabilities. MFPs also incorporate copy functions, scanning features, and the ability to internally store input/output images, which can be sent to designated locations or printed as needed. As information is held within the ‘machine’ functions/ applications to protect stored information from ‘leakage’ have also evolved in the form of security functions and operational design.
Standalone document scanners, on the other hand, have internal buffer memories which enable continuous scanning and communication and are erased as soon as the job is finished. Since there is no need to retrieve and print images asynchronously as with an MFP, the security features required for document scanners are not as sophisticated as those of MFPs.
Network scanners, which operate without a PC, tend to have limited security features such as user authentication functions (ID, password, IC card) and separation of data and control signals. The reason is that document scanners specialise in digitising documents, and scanned images are processed by dedicated software running on a separate server. In PFU’s example, PaperStream NX Manager is responsible for configuring, managing, and executing JOBs. For KODAK ALARIS, INfuse Management Software and other software performs these tasks. Since these software products are run on a server on a corporate LAN security, measures are therefore implemented by the network administration of the organisation. The scanner itself only needs to be able to guarantee user management and secure communication.
In cases where scanned image files are transferred to another system using RPA, etc., the RPA robot itself needs to be misconfigured and the security management of the PC on which the robot is running needs to be well protected.
Conclusion
As the paperless society progresses, the volume of paper documents themselves will decrease and MFPs will be used more as scanners. The convenience of being installed in an office, used by multiple organisations and multiple users, and accessible from the outside via a web interface will not change. This means that security measures will need to be continuously updated.
Scanners, on the other hand, will likely continue to improve in function and performance in the direction of greater convenience as input end-devices. For example, when scanned images are transferred to a designated server or a folder in the cloud, or encrypted and sent as an attachment to a designated email address, security functions that can only be set by the administrator user will be necessary. However, implementing advanced functions, such as MFP-like features to prevent miss-operation and encrypt communications, may increase both the cost of the scanner and the time required for its operation.
Therefore, Infosource believe that the functionality level of network scanners currently on the market is sufficient from a security perspective. We believe that the market will not demand more functionality than that. The security measures would be better handled on the RPA robot and management server side, which would allow for a freer choice of scanners and preserve economy and convenience